Important Tips to Improve Security of your Raspberry Pi
Today, Raspberry Pi board has become one of the most popular tools in the field of electronics and embedded programming. The board’s growing popularity has grown to the point where the platform, about the size of a palm, has attracted the attention of software and security experts. The Raspberry Pi board can be considered a personal computer (with lower processing power than personal computers). But this computer allows the user direct access to the processor bases or GPIO. In this tutorial we will see some Important Tips to Improve Security of your Raspberry Pi boards.
This board can be considered as a personal computer. A personal computer is always at risk of hacking, hacking and stealing information. Raspberry Pi board is no exception to this rule. However, by connecting it to the outside world you basically make the target for different kinds of attacks.

If you are running different services on your Raspberry Pi (like web or ftp server), your little device has even more chances to get attacked. If some of these attacks is successful you can loose the information stored on your device or end as a spam server. Several precaution measures that can make your Pi more secure will be presented in this article. But keep in mind that securing the computer is a complex task and your Pi will never be secure as you are expecting.
Keep your Operating System up to date
Constant updating of the operating system to improve the security of the Raspberry Pi board reduces the likelihood of its vulnerability. As you know, there are several companies involved in software development. Often software has security bugs that after a while, these bugs are fixed by the manufacturer. As a result, by constantly updating your operating system, these bugs will be fixed and the way to penetrate and sabotage through previous security bugs will be eliminated.

The Linux operating system, like any other operating system such as Windows, has various programs installed on it. Software versions, on the other hand, are constantly being updated and developed. With the help of the below command, we can be informed about the latest version of the software.
You can download the latest Raspbian OS from the this link.
Well, the good news that RPi runs on different Linux distributions. In that way you are secured from many malwares, worms and viruses that are present these days and affect Windows based machines. But the good practice is to keep your system updated and patched. Therefore, regularly run package update
sudo apt-get update
sudo apt-get upgrade
If you want to update the operating system in addition to the packages, you must use the following command.
sudo apt dist-upgarde
Change Raspberry Pi Login Information
The Raspberry Pi boards have a default username and password. The password must be changed to prevent possible intrusion and to improve the security of the Raspberry Pi board. First, to create a new password, we do the following. This is one of the most Important Tips to Improve Security of your Raspberry Pi.
sudo passwd {username} {password}
Next, according to what was said in the video, we will create a new username with the following command.
sudo adduser iotstarters
Installing Firewall
Firewall is a tool to control the entry and exit of the operating system. In other words, users’ access to the system, network traffic control, and so on determined by this security tool. We will see how to install a firewall using the command below.
sudo apt install ufw
Installing the above software alone is not enough for the security of the Raspberry Pi board. With the help of this software, we must restrict access to ports. In other words, the way to enter a system is through the port. By setting the login permission by ufw software, we can control the login. It is also important that we discuss a little about the concept of port.
Understanding Concept of Ports on Network
The connection between different computers in the network is very similar to the connection of people with each other in the community. Suppose you want to send a package to a friend who lives in another city through the post office. To send the package through the post office, you need to enter the recipient’s address and name in the postal package. Because in addition to your friend, other family members also live with him and you have to specify who this package should reach.

According to the above scenario, the connection of two computers to each other is possible through the port and IP address. For example, suppose you want to upload a photo to a server. You must have an IP address to connect to the server. But to upload a photo, just having an IP is not enough, you have to use a special file upload protocol, FTP. So you have to connect to the dedicated FTP port, which is usually number 21, and upload your photo. Here, the IP address is the same as the mailing address and the port name is the same as the recipient.
Now that we are familiar with the concept of port and its importance in computer networks, we continue the discussion. As mentioned, the port is the gateway to a computer after IP. With the ufw tool, we have to manage the port. Management means restricting a number of ports. We set access and permission for port 22, which is for ssh communication.
sudo ufw allow 22/tcp comment “SSH Access”
So far, our firewall has not been activated. To activate it, we must follow the following command.
sudo ufw enable/disable
Installing Fail2ban service
One way to hack and log in is to try different combinations of username and password. In other words, a hacker tries to infiltrate the system by trying so many different usernames and passwords to finally log in. A good tool to counter this attack and increase the security of the Raspberry Pi board is to use a tool called fail2ban. This tool helps you to be limited for a certain period of time if an IP tries to log in multiple times. In the following, we will discuss how to install and configure this software. First, install this tool with the following command.
sudo apt install fail2ban
After installing the software, we need to make the necessary settings for it. So go to the following path to open the configuration file for editing
sudo nano /etc/fail2ban/jail.local
Copy and paste the content below. We assume your private IP addresses are in the range 192.168.0.* and if there is 3 failed entry then you will be banned for 15 Min.
# SSH
# 3 failed retry: Ban for 15 minutes
[ssh]
enabled = true
port = ssh
filter = sshd
action = iptables[name=SSH, port=ssh, protocol=tcp]
mail-whois-lines[name=%(__name__)s, dest=%(destemail)s, logpath=%(logpath)s]
logpath = /var/log/auth.log
maxretry = 3
bantime = 900
ignoreip = 192.168.0.0/16
[ssh-ddos]
enabled = true
port = ssh
filter = sshd-ddos
action = iptables[name=SSH, port=ssh, protocol=tcp]
logpath = /var/log/auth.log
maxretry = 10
ignoreip = 192.168.0.0/16
Restart the fail2ban service:
sudo /etc/init.d/fail2ban restart
Check the log file to ensure it is working:
sudo tail -f /var/log/fail2ban.log
Finally, you can activate the service with the following command. This is also a Important Tips to Improve Security of your Raspberry Pi.
sudo systemctl enable –now fail2ban
Change the default SSH Port
As mentioned earlier, ports play a key role in logging into a system. The SSH port is used for full access to a system (remote). By default, the port number on systems such as Raspberry Pi is 22. Here, to increase security, we change the number of this port from the usual state and set a desired number for it. This way, the connection through SSH port to number 22 will no longer be established. Next, to change this number, go to the following address and open the SSH configuration file.
sudo nano /etc/ssh/sshd_config
Change the SSH port number from 22 to the desired number. You can even allow access to certain usernames in this file and block other usernames from being accessed. This is done using the following command.
allowusers {iotstarters,daneshjookit,aghighnet,..}
Now you can restart the SSH service according to the following command.
sudo service ssh restart
Secure SSH
We mostly connect remotely with our Raspberry Pi using SSH protocol. While this is a great way to communicate with your device, it can become major security hole if you are using authentication with weak password. By using brute force attack someone can guess your password and gain access to your system. Thanks to the different distributions of the Linux operating system for this board, working with it will be very attractive. But as security is a key issue in all areas of electronics and computing, there is a risk of intrusion and theft of information on the Raspberry Pi board.
These are brute force attacks performed by automatic scripts which are using dictionaries that contain common usernames and passwords (like username: root, password: 1234). What can you do? At first, use strong password. Secondly, disable remote root login. This can be done through the sshd config files. By changing the line PermitRootLogin to no.
sudo nano /etc/ssh/sshd_config
Other Tutorials:
- Raspberry Pi Temperature Logger DS18B20
- DHT11 Data Logger using Raspberry Pi and Python code
- Raspberry Pi PICO with Thonny IDE
- Connecting DHT11 Sensor with Raspberry Pi 4 / 3 using Python
- IoT Project using Local Blynk Server
- Connecting to Raspberry Pi via Putty
Disabling Unwanted Interface
There are several user interfaces on the Raspberry Pi board. For example, one user interface is responsible for connecting the Raspberry Pi camera, another for GPIO control, and another interface for controlling network and Wi-Fi connections. To disable additional interfaces, we must enter the Raspberry Pi settings with the following command or you can login to raspberry pi and navigate to Raspberry Pi Configuration for GUI based console. Some of these are Important Tips to Improve security of your Raspberry Pi board.
sudo raspi-config
The Raspberry Pi Configuration GUI console is displayed.
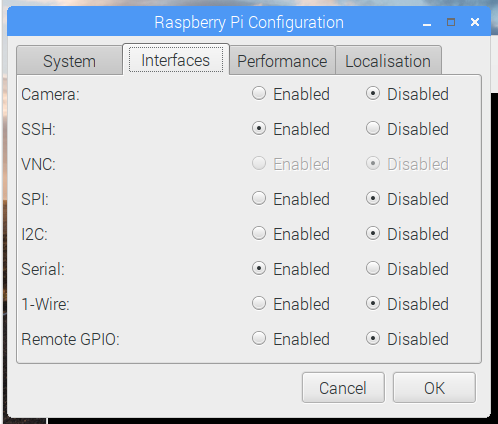
On the Interfacing Options section, disable the desired user interface depending on your needs. For example, by disabling the Wi-Fi interface, we can prevent hackers from trying to infiltrate Raspberry Pi using Wi-Fi.
Monitoring Ports and Services
As mentioned earlier, ports play one of the most sensitive roles in establishing communication between the user and the computer. By monitoring the ports and services running on the port, if the unauthorized user has logged in, its details will be displayed. For this, enter the following command in the terminal.
netstat -an
By entering the above command, a list of ports and running services based on the port will be displayed.
Conclusion
Security is a concept that only means peace. As our physical and physical security is the most important challenge for survival, maintaining the security of hardware and software systems is vital to digital survival. If in the past, our concern was security at home and at work, today security locks for personal computers, servers, electronic boards and hardware are considered important.
By taking the issue of network and computer systems more seriously, including making the right settings in the system, constantly updating, determining the level of access and changing the default username and password of the systems. System vulnerabilities can be reduced, security gets increased and this minimize the penetration.
